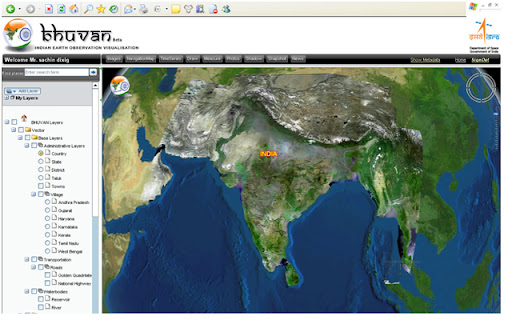
Monday, December 27, 2010
25)Blog
4)Digital Certificate
3)Cookie
Is a piece of text stored by a users web browser that can contain anything even personal information.
1)ActiveX
Tuesday, December 21, 2010
25)Time bomb
24)Teleconferencing
21)Pyramid Scheme
18)Logic Bomb
It is a programming code added to the software of an application or operating system that is set to activate at a certain time. It is similar to a Trojan Horse.
17)hoax
16)Fraud
15)Filtering
14)Windows Mail
11)Spam
10)Signature
Signature is a code or a type of writing that can be sended and will be identified to the sender
Subscribe to:
Comments (Atom)